
A phishing email is a type of cyber-attack and a common cybersecurity threat through which hackers attempt to trick you to get your confidential and sensitive data without your knowledge or consent.
The first question that might come to your mind may be why should you care about phishing emails and how can they harm you? The answer is evident from the large volume of phishing emails circulating the globe every day.
74% of organizations experienced a successful phishing attack during 2020 in the USA alone. This is 14 % higher than the previous year.
Your personal information is one of your main assets in a digital world. Hackers and cybercriminals want to steal this asset from you. They can then misuse this stolen information and, as a result, you could experience financial loss or identity theft.
In this article, you will learn about phishing emails and the ways to recognize them. You will also learn what to do if you receive a phishing email. So, if you are a victim of a cyberattack or want to save yourself from phishing attacks, then keep on reading!
Phishing Email Definition
You may ask, what is the definition of phishing? According to the University of Virginia, phishing is a fraudulent attempt to steal personal information.
In other words, it can be defined as a technique used by hackers to trick you into revealing sensitive information such as credit card numbers or social security numbers. Other examples are, bank information, IDs, and/or passwords.
It is also called specifically a phishing email because fraud companies or individuals often contact you in the form of emails to attempt to persuade you to give up details about your private information.
Among phishing attacks, about 96% are performed via sending emails to people. The remaining attempts are carried out through malicious websites and text messages.
The attackers may send you an email, which looks like it is coming from a reputable and reliable source, then they ask you to perform some action (like clicking a link or button) as a reply to their email. A phishing email normally contains a link that takes you to a web form or fraudulent website.
Once you are on the fake website, the hacker tries to get you to enter your personal information. After that, hackers are able to access to your emails, banks, and other accounts.
Sometimes these emails will contain malicious file or software. This file will download to your device and then can send your personal information to the phisher without your permission.
A phishing email is a common concern for businesses, large organizations, and universities. Yet, small companies and individuals, like you, are also not safe.
Hackers launch thousands of phishing emails every day, many of which are successful in stealing information. This causes people to lose millions of dollars each year. A report from the FBI says that people lost $57 million in 2019 to phishing schemes.
As of Jan 17, 2021, Google has registered 2,145,013 phishing sites. This is 27 % more than the phishing sites that were registered in 2020.
Email Phishing Examples
The main reason why people get tricked is that these emails look like they are coming from a company you know. Some examples are your bank, an online payment service, a social media site, an online store, etc.
To look real, the attackers will often use the company’s logo and header. Then, they sometimes tell you a fancy story to trick you so that you click on the link or open an attachment. The following are some examples of what they may say to scam you:
- they have noticed suspicious login attempts on your account
- you have problems with your payment account, so you need to re-enter your credentials
- you are eligible for a refund, so apply with your information
- you got a free coupon
All these examples aim to pique your interest so that you can give your personal information to them.
How to Recognize a Phishing Email
The main issue here is how can we recognize a phishing email if it looks so legitimate? The following are some clues that may help you detect a phishing email.
Checking the Domain Name:
We can detect a phishing email by checking the domain name in the sender’s email. A domain name is the second half of any email address written after the “@” symbol.
Legitimate companies send emails ending with their domain name (usually the company name). They usually do not send messages from a public email domain such as gmail.com or hotmail.com.
Most of us usually read the name of the sender, however, we may not look at the second part of the email address (aka the domain name) for where the email is coming from. Hackers take advantage of this negligence. They use fake domain names which seem like an original address.
For instance, michelle@paypal.com is an example of the original email. Whereas michelle@paypal23.com or paypal@notice-access-273.com are examples of scam emails.
Unfortunately, including the names of famous organizations is usually enough to trick people. Because most of us just look at that name (say PayPal) and become satisfied that it is legitimate. Most people do not bother to check the difference between the actual domain name and its look alike.
Pro Tip: We should not only check the sender’s name but also look at the domain name in the sender’s email address.
Sense of Urgency Is Created:
Another way to spot a phishing email is by recognizing the sense of urgency it creates. It is a tactic used by hackers to instill urgency in the company or individual so that the victim immediately provides all the information to the hackers.
The attackers give very little time to respond. They tell you that the deal will end or your account will be suspended if you don’t respond right away. The more time a user gets, the more likely the user will notice things that are wrong in the email.
This tactic is very commonly used by data thieves. If you come across such an email demanding an urgent reply, simply ignore the email. Then, you can contact the source directly by phone or by visiting them. Remember that reliable organizations will never ask you to act fast or lose out on something.
Pro Tip: Do not provide your personal information on any email that creates a sense of urgency, unless you are sure about its genuineness.
Cybercriminals Force You to Their Website:
Sometimes phishing emails are coded entirely as a hyperlink. This means that the entire email works as a hyperlink. By clicking anywhere on the email, it will bring you to a fake web page, or will download malware (a virus) onto your computer.
The purpose of these emails is to forcibly take you to their website or to enter a virus into your computer without your permission. Legitimate companies would never force you to their website.
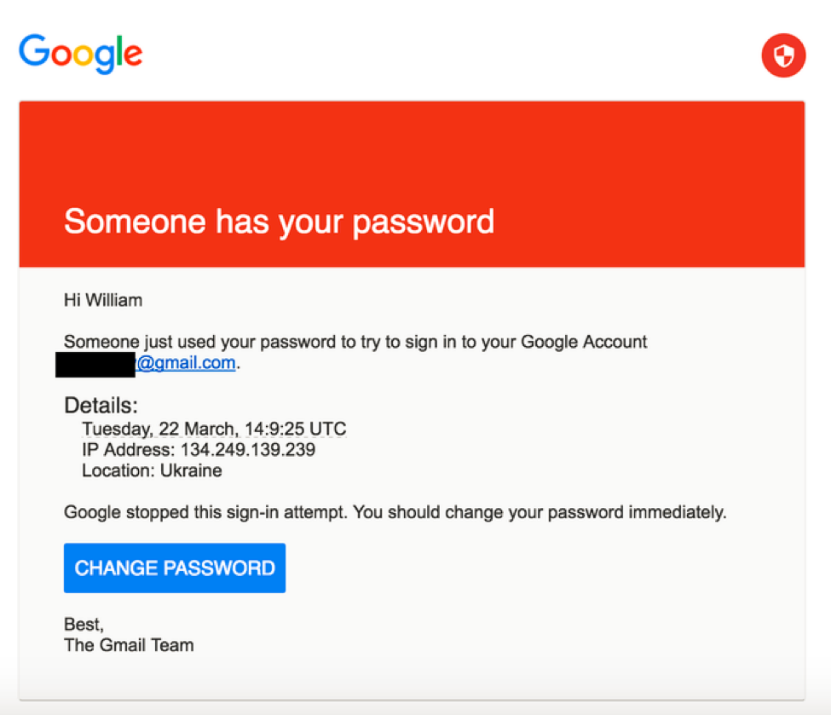
Below is a perfect example, which is taken from https://www.thesslstore.com/, of creating a sense of urgency. It also shows how hackers can force you to a fake website to steal your personal information.
Pro Tip: Any email which forces you to their website is almost certainly a scam, so don’t click anywhere in the email if you can catch this.
Not Calling You by Name:
Legit companies usually call you by your name. While most hackers use generic greetings in their phishing emails. For example, dear customer, dear account holder, respected member, etc.
Hackers use these terms to dodge you. They ask for your personal information pretending as a permissible company. A legit organization will usually always call you by your name and would direct you to contact via phone.
Sometimes, they call you by your name but want you to confirm that this is your email. For example, they will greet you with your name and then they would inform you that they are trying to email you but they have not been successful due to some technical problem e.g., unreachable IP address.
Pro Tip: My advice would be to make sure the email is authentic and then reply to it.
Poorly Written Emails:
The easiest way to detect a scam or phishing email is through bad grammar. The sentences used in the email could also be out-of-context. The legitimate companies send their emails with proper grammar and information. They pay attention to details and they also don’t make grammatical mistakes.
This is because legit companies have qualified staff to send emails to their clients. On the other side, hackers purposely write emails with mistakes. They often want to check how much attention the reader is giving to the email.
The idea is to weed out anyone that can pick out the grammatical mistakes. If they can’t or don’t pay close enough attention, there is a better chance that they might not figure out the scam. The other reason is that, often times, attackers are not the best writers.
Pro Tip: Always look for grammatical mistakes, not just the spelling, in doubtful emails.
Suspicious Attachments or Links:
An official email does not contain any malicious or unsolicited attachments or links. They do not send you attachments via email randomly. Instead, they will direct you to their official website to download the required file.
If you are not expecting any file in the email or the attachment makes no sense, then don’t open it.
An infected attachment is any email that contains malware (a type of computer virus). It looks like that the attachment is for you (like an invoice of items you purchased).
When you open the attachment, you will find that the attachment isn’t intended for you. But, after that, it’s too late because as the document is opened it unleashes the malware onto your computer.
Pro Tip: Never open any attachment until you are 100 % sure that the mail is from a genuine party.
The Domain Name Is Misspelled:
Another clue that is often hidden and may not be visible at first glance is a misspelled domain name. It can be difficult to spot a spoofed domain name, so look carefully.
Mostly, ‘m’ is written as ‘r’ and ‘n’ in popular website addresses. For example, ‘gimletmedia.com’ can be replaced with ‘gimletrnedia.com’. and ‘www.bankofamerica.com’ with ‘www.bankofarnerica.com’.
Pro Tip: Be careful and remember this type of tactic is used frequently by hackers.
What to do if you receive phishing (suspicious) emails?
If you receive an email that seems suspicious and you are not sure about its authenticity, then follow these tips:
- do not respond
- do not click on any link that is given in the email and not open any attachments
- do not acknowledge the email in any way
- do not click anywhere in the email because some emails work as a hyperlink
- for a permanent solution delete the email or report spam
Do you think you have already responded to a phishing email and they got your information? You need to immediately contact the respective government agency in your country. For example, in the USA you can contact https://www.identitytheft.gov/ to protect yourself.
There are government agencies in your country where you can report a phishing email. In the USA, you can report to the Anti-Phishing Working Group at reportphishing@apwg.org. Alternatively, you can report to the FTC at ReportFraud.ftc.gov if you receive a phishing email.
How to Protect Yourself from Phishing Emails
Most email service providers (say Gmail) include the spam filter feature. This feature keeps phishing emails out of your inbox. However, cybercriminals are always trying to outperform these filters.
It means we need extra layers of protection besides relying on spam filters. You may take the following five steps to protect yourself from phishing.
Install Security Software on your Computer
Install and regularly update antivirus software on your computer so that it can handle any new security threat if you unwantedly got phished.
If you think some software has downloaded when you clicked the link or opened an attachment, then run antivirus software to scan your computer.
Set Software to Automatically Update in your Mobile Phone
These mobile updates can give you protection against several types of security threats.
Use Multi-level Authentication to Protect your Accounts
Multi-level authentication means providing multiple steps for authorization. This feature offers extra security by demanding your authentication in multiple ways and thus makes it harder to break into accounts.
Multi-level authentication asks for your credentials like a password, passcode, or pattern. Then it asks for things that cannot be stolen or hacked like your fingerprint, face locks, or retina scan.
Multi-level authentication makes it harder for hackers to log in to your accounts. Even if they do get your username and password, they couldn’t get your fingerprint, face, or retina. That’s why multi-level authentication is difficult for hackers to hack.
Always Back Up your Important Data
You can back up your data by copying it to any other device, an external hard disk, or cloud storage. But remember, if you are backing up your data onto any device, do not connect that device to any kind of network.
Check the Link Before Clicking
Before clicking a link, hover over it to see the actual URL the link is pointing to. Secure websites with a valid SSL certificate always start with ‘https://’.
Conclusion
To conclude, phishing emails are a commonly occurring problem in this digital age, but it can be easily handled if we change our browsing style. We need to be more careful, aware, and vigilant, especially when it comes to entering our personal and sensitive information.
We can also get support from different software (e.g., spam filters and antivirus software) and set up vital browsers settings to protect ourselves. You can also hire a Cybersecurity Services Provider to help keep you safe.
Related questions
How to report phishing emails in outlook?
To report a message as phishing in Outlook follow these steps
- In the message list, select the message or messages you want to report.
- Above the reading pane, select Junk > Phishing > Report to report the message sender.
How to report phishing emails to apple?
- If you receive a suspicious email, please forward it to reportphishing@apple.com.
- To report spam that you receive in your iCloud.com, me.com, or mac.com inbox, send them to abuse@icloud.com.
- To report spam that you receive through iMessage, tap “Report Junk” under the message. You can also block unwanted messages and calls.
What is a spear-phishing email?
Spear phishing is an email targeted towards a specific individual, organization, or business. It is often intended to steal data for malicious purposes. Cybercriminals may also intend to install malware on a targeted user's computer.